Firewall Rules
Riverbed Edge requires the following inbound and outbound network access. It does not require any firewall inbound access from the public Internet to your corporate network. Refer to the diagram and table below for a visualization![]() A runbook node category that shows data in a chart, graph, table, or note, providing visual representation of analysis results in runbook output. of the firewall rules as well as the Service, Protocol, DNS, Targets, Port, and Descriptions of the rules.
A runbook node category that shows data in a chart, graph, table, or note, providing visual representation of analysis results in runbook output. of the firewall rules as well as the Service, Protocol, DNS, Targets, Port, and Descriptions of the rules.
Refer to Configuring Riverbed IQ Ops and and Data Sources for how this information is used during the Riverbed Edge configuration process.
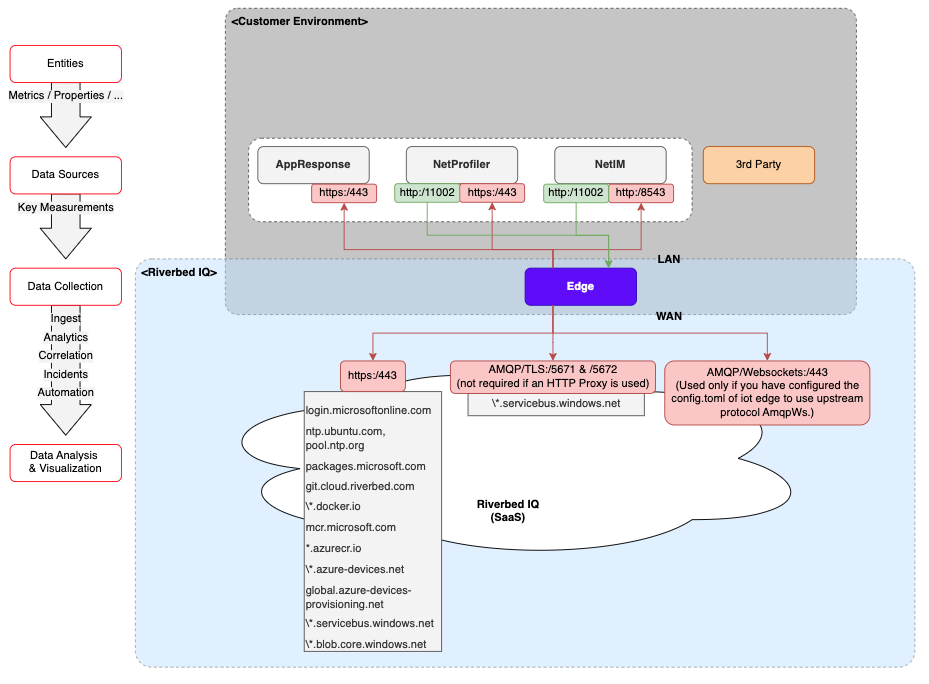
Diagram: Riverbed IQ Ops Connectivity (as enabled by Firewall Rules)
| Service/Protocol | From | To | DNS Targets | Port | Description |
| HTTPS | Riverbed Edge (LAN) |
NetProfiler (LAN) AppResponse (LAN) |
443 | Enables secure communications between Riverbed Edge and Riverbed Data Sources |
|
| HTTPS | Riverbed Edge (LAN) | NetIM (LAN) | 8543 | ||
| HTTP |
NetProfiler (LAN) NetIM (LAN) |
Riverbed Edge (LAN) |
11002 | ||
| HTTP | Riverbed Edge(LAN) | Internet (WAN) | 80 | Linux [apt] command-line utility for installing, updating, removing, and otherwise managing packages on Ubuntu Linux distributions. | |
| HTTPS | Riverbed Edge (LAN) | Internet (WAN) | login.microsoftonline.com | 443 | Authentication service. |
|
ntp.ubuntu.com pool.ntp.org |
Enables accurate time-synchronization. | ||||
|
packages.microsoft.com security.ubuntu.com archive.ubuntu.com |
Installation and upgrade of Riverbed Edge components. | ||||
| git.cloud.riverbed.com | Access to configuration and software for Riverbed Edge runtime modules. | ||||
| *.docker.io |
Enables secure communications between Riverbed Edge and Riverbed SaaS. Supported protocols: AMQP, MQTT, and HTTPs. |
||||
| mcr.microsoft.com | |||||
| *.azurecr.io | |||||
| *.azure-devices.net | |||||
| global.azure-devices-provisioning.net | Enables secure upload of observability data from Riverbed Edge to Riverbed SaaS. | ||||
| *.servicebus.windows.net | |||||
| *.blob.core.windows.net | |||||
| AMQP over TLS | Riverbed Edge (LAN) | Internet (WAN) | \*.servicebus.windows.net | 5671 5672 Not required if an HTTP proxy is used. |
(default config) |
| AMQP over Websockets | Riverbed Edge (LAN) | Internet (WAN) | 443 | Only used if you have configured the config.toml of Riverbed Edge to use upstream protocol AmqpWs. |
Table: Riverbed IQ Ops Firewall Rules (to enable Riverbed IQ Ops Connectivity)